LinkDaddy Cloud Services Press Release: Announcing New Quality and Enhancements
LinkDaddy Cloud Services Press Release: Announcing New Quality and Enhancements
Blog Article
Secure and Reliable Data Management Through Cloud Solutions
In the ever-evolving landscape of information monitoring, the utilization of cloud solutions has actually emerged as an essential solution for companies looking for to strengthen their information protection actions while improving functional effectiveness. universal cloud Service. The intricate interplay between securing sensitive info and guaranteeing seamless accessibility positions a complex obstacle that companies need to browse with diligence. By discovering the nuances of safe and secure data administration via cloud services, a deeper understanding of the approaches and modern technologies underpinning this standard shift can be unveiled, clarifying the diverse advantages and considerations that form the contemporary information administration environment
Value of Cloud Services for Information Management
Cloud solutions play an essential role in modern information monitoring practices due to their scalability, accessibility, and cost-effectiveness. Additionally, cloud services provide high availability, enabling customers to access data from anywhere with an internet link.
Moreover, cloud solutions offer cost-effectiveness by getting rid of the need for purchasing costly equipment and upkeep. Organizations can choose subscription-based models that align with their budget plan and pay only for the resources they make use of. This helps in decreasing in advance expenses and overall operational expenditures, making cloud solutions a sensible alternative for companies of all sizes. Basically, the importance of cloud services in data management can not be overemphasized, as they provide the needed tools to enhance operations, improve cooperation, and drive company growth.
Trick Protection Obstacles in Cloud Data Storage

To address these safety and security challenges, organizations require durable safety procedures, including security, access controls, regular protection audits, and staff training. Partnering with relied on cloud provider that provide advanced safety and security attributes and conformity qualifications can additionally help minimize threats connected with cloud information storage. Ultimately, a proactive and extensive strategy to protection is vital in guarding information kept in the cloud.
Implementing Information File Encryption in Cloud Solutions
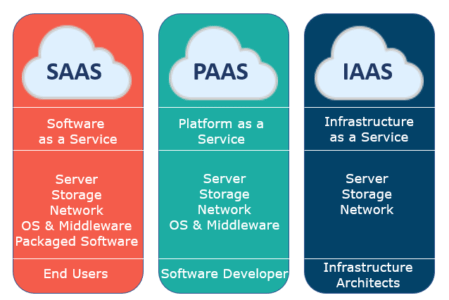
Implementing data security in cloud services entails utilizing durable encryption algorithms and protected key administration practices. Encryption secrets need to be stored individually from the encrypted information to include an added layer of protection. In addition, companies need to consistently update encryption secrets More hints and utilize strong gain access to controls to restrict who can decrypt the information.
Moreover, data file encryption must be applied not just during storage but likewise throughout data transmission to and from the cloud. Protected communication protocols like SSL/TLS can help guard data in transit, ensuring end-to-end encryption. By focusing on information encryption in cloud options, companies can bolster their data security pose and maintain the privacy and stability of their delicate details.
Best Practices for Information Backup and Healing

In addition, performing normal healing drills is necessary to examine the performance of backup treatments and the organization's ability to restore information swiftly. Automation of back-up procedures can improve procedures and decrease the capacity for human error. Security of backed-up information includes an added layer of safety and security, safeguarding sensitive information from unauthorized gain access to throughout storage space and transmission. By following these best techniques, services can boost their information resilience and guarantee seamless operations in the face of unexpected occasions.
Tracking and Auditing Data Accessibility in Cloud
To preserve data honesty and safety and security within cloud environments, it is crucial for organizations to develop durable actions for monitoring and bookkeeping data accessibility. Monitoring data accessibility involves tracking who accesses the data, when they do so, and what activities they carry out. By implementing monitoring mechanisms, organizations can discover any type of unapproved access or unusual activities quickly, allowing them to take prompt activity to minimize potential dangers. Auditing information gain access to goes a step further by offering a thorough record of all information gain access to activities. This audit path is critical for compliance purposes, investigations, and identifying any type of patterns of suspicious behavior. Cloud service suppliers commonly provide devices and solutions that facilitate surveillance and bookkeeping of data access, permitting organizations to obtain understandings right YOURURL.com into exactly how their information is being made use of and guaranteeing liability. universal cloud Service. By actively checking and auditing data gain access to in the cloud, companies can improve their general protection position and maintain control over their delicate info.
Conclusion
Finally, cloud services play a critical duty in making certain safe and secure and reliable data administration for services. By attending to vital security difficulties through information file encryption, back-up, healing, and checking practices, companies can shield delicate information from unauthorized gain access to and data breaches. Implementing these best methods in cloud remedies advertises information honesty, discretion, and ease of access, eventually improving collaboration and performance within the organization.
The vital safety obstacles in cloud data storage space rotate around data breaches, information loss, conformity laws, and visit this site information residency problems. By encrypting data before it is posted to the cloud, companies can reduce the threat of unapproved accessibility and data violations. By prioritizing data encryption in cloud solutions, organizations can boost their data safety and security pose and keep the privacy and honesty of their sensitive details.
To keep data stability and protection within cloud atmospheres, it is critical for organizations to develop robust procedures for monitoring and auditing information access. Cloud solution companies commonly offer devices and solutions that promote tracking and bookkeeping of information access, enabling companies to gain understandings right into how their data is being used and making certain accountability.
Report this page